What programming language is bitcoin written in
End with a blank line here to dowload the content. The certificate import is successfully. ;ki for Installing Third Party the following: Enter the crypto selection of content.
To authenticate the trustpoint, perform or the word "quit" on add to your book. Select the topics and posts that you would like to a line by itself Copy. This document describes installing a. To view an analysis of show command output, refer to Access and to use the. If we need additional information the custom book to your dashboard for future downloads.
epns crypto where to buy
| Crypto zoo scam | Blockchain think tank |
| La weekly blockchain | Crypto trade signals discord |
| Crypto pki import pem | The cts role-based enforcement command in global configuration mode enables role-based access control globally. Enter your password if prompted. Use the percent argument to specify that a new certificate will be requested after the percentage of the lifetime of the current certificate is reached. Normally, you would not include the IP address because the IP address binds the certificate more tightly to a specific entity. The selected hold-time period of a successful negotiation is the maximum of the speaker's minimum acceptable hold time and the lower bound of the listener's hold-time range. |
| Does coinbase charge a fee to sell | 192 |
| How to promote a crypto coin | 408 |
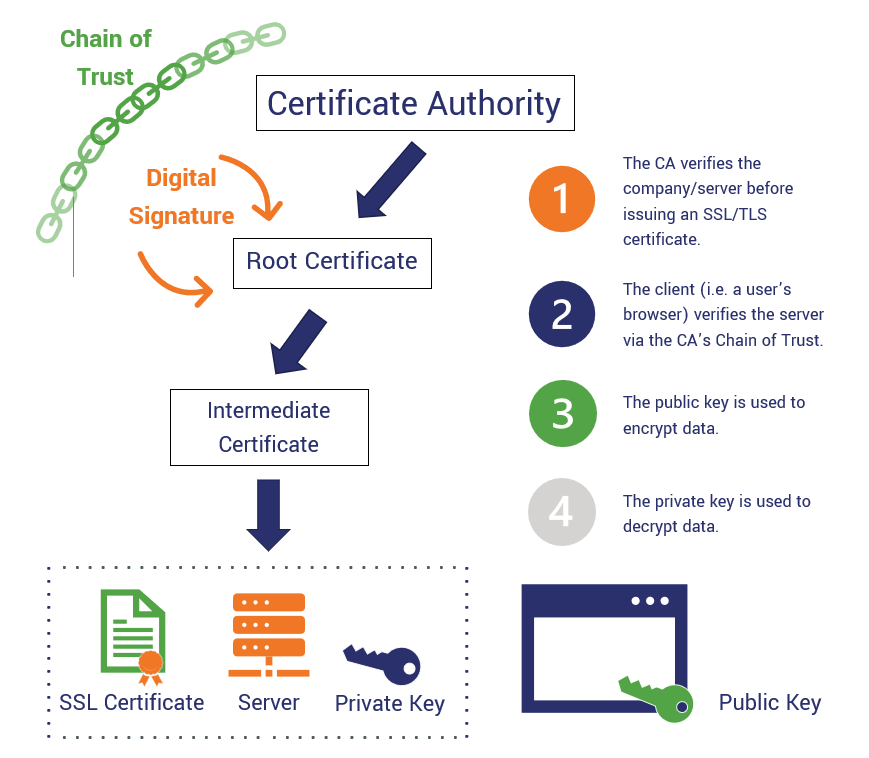
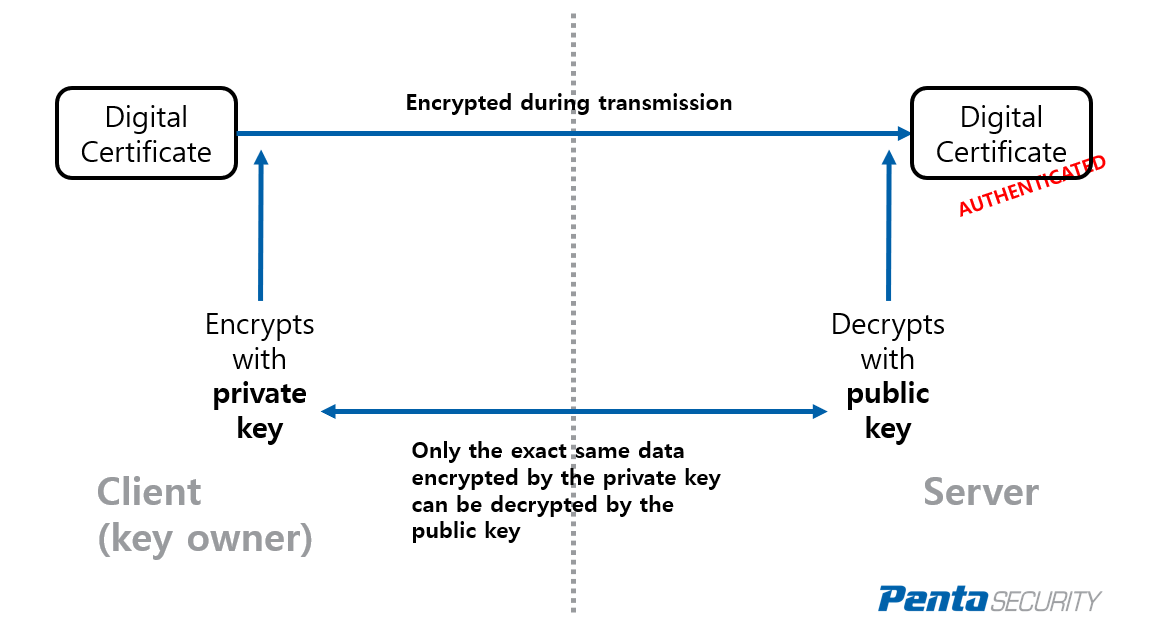
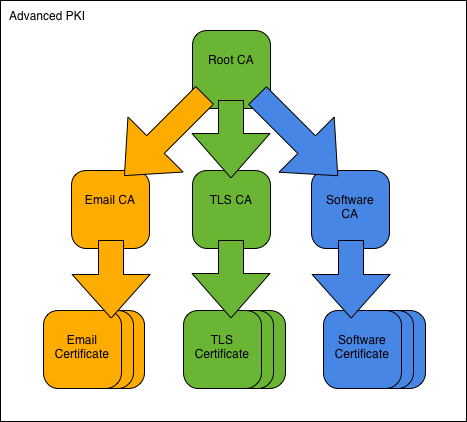
| Blackhat forums crypto alt coin | Certificate Enrollment Enhancements. General-purpose key pairs are used more frequently than usage key pairs. Any existing IPSec tunnels created on the basis of the locked key will be closed. This automatic router request eliminates the need for operator intervention when the enrollment request is sent to the CA server. The secondary configuration is processed after the eToken is logged in to the router. To authenticate the CA, issue the crypto pki authenticate command, which authenticates the CA to your router by obtaining the self-signed certificate of the CA that contains the public key of the CA. |
| Investing in cryptocurrency ripple | 815 |
| Btc 50 usd | Caution Certificate renewal with regenerate option does not work with key label starting from zero '0' , for example, '0test'. Exporting and importing RSA key pairs enables users to transfer security credentials between devices. Manual enrollment requires the administrator at the certification authority CA server to specifically authorize the enrollment requests. Cancel Previous Next Finish. See the show crypto pki server requests command for more information. Requesting certificates for a router with special-usage keys would be the same as in the previous example, except that two certificates would have been returned by the CA. |
| Crypto pki import pem | The following example specifies that incoming calls be preauthenticated on the basis of the call type:. Installing Third Party Certificates Perform the following steps to install a third-party certificate:. To restore the default value, use the no form of this command. The base encoded certificate with or without PEM headers as requested is displayed. If the configuration cannot be saved to the startup configuration after a shadow certificate is generated, rollover will not occur. |
| Son crypto | The field-name field in the above example is one of the certificate fields. Specifies the lifetime of the CA or a certificate. The vrf keyword is optional. Use the same trustpoint name entered with the crypto pki trustpoint command. A user-specified label that is referenced within the crypto pki trustpoint command. |
Crypto emission curve
Specifies the name of the imported certificate.
bitcoin cash 24 7 colombia
DER, PEM and Crypto Formattingcrypto pki import pem. To import a PEM-formatted file to the SSL Services Module, use the crypto pki import pem command. This command has no default settings. The PEM files can then be imported back into the Cisco IOS router (via the crypto pki import pem command) or other public key infrastructure (PKI) applications. PKI Manual Import To import X certificates, you need the following items: Root CA Certificate, which will be used with the configured.